Difference between revisions of "Creating a RHEL KVM Networked Bridge Interface"
(Created page with "{{#pagetitle: Creating a RHEL 8 KVM Networked Bridge Interface }} <table border="0" cellspacing="0" width="100%"><tr> <td width="20%">Creating KVM Virtual Machines on RHEL w...") |
(No difference)
|
Revision as of 19:51, 10 June 2019
| Previous | Table of Contents | Next |
| Creating KVM Virtual Machines on RHEL 8 with virt-install and virsh | Managing KVM on RHEL 8 using the virsh Command-Line Tool |
|
You are reading a sample chapter from the Red Hat Enterprise Linux 8 (RHEL 8) Essentials book. Purchase a full copy of Red Hat Enterprise Linux 8 (RHEL 8) Essentials in eBook ($9.99) or Print ($36.99) format Red Hat Enterprise Linux 8 Essentials Print and eBook (ePub/PDF/Kindle) editions contain 31 chapters and over 250 pages |
By default, the KVM virtualization environment on RHEL 8 only creates a virtual network to which virtual machines may connect. The goal of this chapter is to cover the steps involved in creating a network bridge on RHEL 8 enabling guest systems to share one or more of the host system’s physical network connections.
Network bridges may be configured on RHEL 8 either by manually using the NetworkManager command-line tool, or via the Cockpit web interface.
Virtual Networks and Network Bridges
A KVM virtual machine running on RHEL 8 has two options in terms of networking connectivity.
One option is for it to be connected to a virtual network running within the operating system of the host computer. In this configuration any virtual machines on the virtual network can see each other but access to the external network is provided by NAT). When using the virtual network and NAT, each virtual machine is represented on the external network (the network to which the host is connected) using the IP address of the host system. This is the default behavior for KVM virtualization and generally requires no additional configuration. Typically, a single virtual network is created by default, represented by the name default and the device virbr0.
In order for guests to appear as individual and independent systems on the external network (i.e. with their own IP addresses), they must be configured to share a physical network interface on the host. This is achieved by configuring a network bridge interface on the host system to which the guests can connect. In the remainder of this chapter we will cover the steps necessary to configure a RHEL 8 network bridge for use by KVM-based guest operating systems.
Getting the Current Network Settings
A network bridge can be created using the NetworkManager command-line interface tool (nmcli). The NetworkManager is installed and enabled by default on RHEL 8 systems and is responsible for detecting and connecting to network devices in addition to providing an interface for managing networking configurations.
A list of current network connections on the host system can be displayed as follows:
# nmcli con show NAME UUID TYPE DEVICE eno1 99d40009-6bb1-4182-baad-a103941c90ff ethernet eno1 virbr0 7cb1265e-ffb9-4cb3-aaad-2a6fe5880d38 bridge virbr0
In the above output we can see that the host has an Ethernet network connection established via a device named eno1 and the default bridge interface named virbr0 provides access to the NAT-based virtual network to which KVM guest systems are connected by default.
Similarly, the following command can be used to identify the devices (both virtual and physical) that are currently configured on the system:
# nmcli device show GENERAL.DEVICE: eno1 GENERAL.TYPE: ethernet GENERAL.HWADDR: AC:16:2D:11:16:73 GENERAL.MTU: 1500 GENERAL.STATE: 100 (connected) GENERAL.CONNECTION: bridge-slave-eno1 GENERAL.CON-PATH: /org/freedesktop/NetworkManager/ActiveConnection/8 WIRED-PROPERTIES.CARRIER: on IP4.GATEWAY: -- IP6.GATEWAY: -- IP6.ROUTE[1]: dst = ff00::/8, nh = ::, mt = 256, table=255 GENERAL.DEVICE: wlp0s20u4 GENERAL.TYPE: wifi GENERAL.HWADDR: 76:7F:AB:8A:AB:75 GENERAL.MTU: 1500 GENERAL.STATE: 30 (disconnected) GENERAL.CONNECTION: -- GENERAL.CON-PATH: -- GENERAL.DEVICE: virbr0 GENERAL.TYPE: bridge GENERAL.HWADDR: 52:54:00:59:30:22 GENERAL.MTU: 1500 GENERAL.STATE: 100 (connected) GENERAL.CONNECTION: virbr0 GENERAL.CON-PATH: /org/freedesktop/NetworkManager/ActiveConnection/2 IP4.ADDRESS[1]: 192.168.122.1/24 IP4.GATEWAY: -- IP4.ROUTE[1]: dst = 192.168.122.0/24, nh = 0.0.0.0, mt = 0 IP6.GATEWAY: -- . .
The above partial output indicates that the host system on which the command was executed contains a physical Ethernet device (eno1), a physical Wi-Fi device (wlp0s20u4) and the virtual bridge (virbr0).
The virsh command may also be used to list the virtual networks currently configured on the system:
# virsh net-list --all Name State Autostart ----------------------------------------- default active yes
At this point, the only virtual network present is the default network provided by virbr0. Now that some basic information about the current network configuration has been obtained, the next step is to create a network bridge connected to the physical network device (in this case the device named eno1).
Creating a Network Bridge from the Command-Line
The first step in creating the network bridge is to add a new connection to the network configuration. This can be achieved using the nmcli tool, specifying that the connection is to be a bridge and providing names for both the connection and the interface:
# nmcli con add ifname br0 type bridge con-name br0
Once the connection has been added, a bridge slave interface needs to be established between physical device eno1 (the slave) and the bridge connection br0 (the master) as follows:
# nmcli con add type bridge-slave ifname eno1 master br0
At this point, the NetworkManager connection list should read as follows:
# nmcli con show NAME UUID TYPE DEVICE br0 c2fa30cb-b1a1-4107-80dd-b1765878ab4f bridge br0 bridge-slave-eno1 21e8c945-cb94-4c09-99b0-17af9b5a7319 ethernet eno1 virbr0 a877302e-ea02-42fe-a3c1-483440aae774 bridge virbr0
The next step is to start up the bridge interface. If the steps to configure the bridge are being performed over a network connection (i.e. via SSH) this step can be problematic because the current eno1 connection must be closed down before the bridge connection can be brought up. This means that the current connection will be lost before the bridge connection can be enabled to replace it, potentially leaving the remote host unreachable.
If you are accessing the host system remotely this problem can be avoided by creating a shell script to perform the network changes. This will ensure that the bridge interface is enabled after the eno1 interface is brought down, allowing you to reconnect to the host after the changes are complete. Begin by creating a shell script file named bridge.sh containing the following commands:
#!/bin/bash nmcli con down eno1 nmcli con up br0
Once the script has been created, execute it as follows:
# sh ./bridge.sh
When the script executes, the connection will be lost when the eno1 connection is brought down. After waiting a few seconds, however, it should be possible to reconnect to the host once the br0 connection has been activated.
If you are working locally on the host, the two nmcli command can be run within a terminal window without any risk of losing connectivity:
# nmcli con down eno1 # nmcli con up br0
Once the bridge is up and running, the connection list should now include both the bridge and the bridge-slave connections:
# nmcli con show NAME UUID TYPE DEVICE br0 c2fa30cb-b1a1-4107-80dd-b1765878ab4f bridge br0 bridge-slave-eno1 21e8c945-cb94-4c09-99b0-17af9b5a7319 ethernet eno1 virbr0 a877302e-ea02-42fe-a3c1-483440aae774 bridge virbr0 eno1 375d3453-742e-4fef-913e-ec8d0f734706 ethernet --
Note that the eno1 connection is still listed but is actually no longer active. To exclude inactive connections from the list, simply use the --active flag when requesting the list:
# nmcli con show --active NAME UUID TYPE DEVICE br0 c2fa30cb-b1a1-4107-80dd-b1765878ab4f bridge br0 bridge-slave-eno1 21e8c945-cb94-4c09-99b0-17af9b5a7319 ethernet eno1 virbr0 a877302e-ea02-42fe-a3c1-483440aae774 bridge virbr0
Declaring the KVM Bridged Network
At this point, the bridge connection is present on the system but is not visible to the KVM environment. Running the virsh command should still list the default network as being the only available network option:
# virsh net-list --all Name State Autostart Persistent ---------------------------------------------------------- default active yes yes
Before the bridge can be used by a virtual machine it must be declared and added to the KVM network configuration. This involves the creation of a definition file and, once again, the use of the virsh command-line tool.
Begin by creating a definition file for the bridge network named bridge.xml that reads as follows:
<network> <name>br0</name> <forward mode="bridge"/> <bridge name="br0" /> </network>
Next, use the file to define the new network:
# virsh net-define /tmp/bridge.xml
Once the network has been defined, start it and, if required, configure it to autostart each time the system reboots:
# virsh net-start br0 # virsh net-autostart br0
Once again list the networks to verify that the bridge network is now accessible within the KVM environment:
# virsh net-list --all Name State Autostart Persistent ---------------------------------------------------------- br0 active yes yes default active yes yes
Using a Bridge Network in a Virtual Machine
To create a virtual machine that makes use of the bridge network, use the virt-install --network option and specify the br0 bridge name. For example:
virt-install --name MyFedora --memory 1024 --disk path=/tmp/myFedora.img,size=10 --network network=br0 --os-variant fedora29 --cdrom /home/nas/Downloads/Fedora-Server-dvd-x86_64-29-1.2.iso
When the guest operating system is running it will appear on the same physical network as the host system and will no longer be on the NAT-based virtual network.
To modify an existing virtual machine so that it uses the bridge, use the virsh edit command. This command loads the XML definition file into an editor where changes can be made and saved:
# virsh edit GuestName
By default, the file will be loaded into the vi editor. To use a different editor, simply change the $EDITOR environment variable, for example:
# export EDITOR=gedit
To change from the default virtual network, locate the <interface> section of the file which will read as follows:
<interface type='network'>
<mac address='52:54:00:3e:fd:08'/>
<source network='default'/>
<model type='virtio'/>
<address type='pci' domain='0x0000' bus='0x01' slot='0x00' function='0x0'/>
</interface>
Change the source network property from default to br0 then save the file:
<interface type='network'>
<mac address='52:54:00:3e:fd:08'/>
<source network='br0'/>
<model type='virtio'/>
<address type='pci' domain='0x0000' bus='0x01' slot='0x00' function='0x0'/>
</interface>
If the virtual machine is already running, the change will not take effect until it is restarted.
Creating a Bridge Network using nm-connection-editor
If either local or remote desktop access is available on the host system, much of the bridge configuration process can be performed using the nm-connection-editor graphical tool. To use this tool, open a Terminal window within the desktop and enter the following command:
# nm-connection-editor
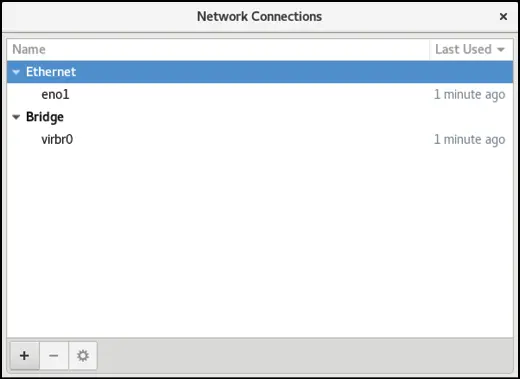
When the tool has loaded, the window shown in Figure 23-1 will appear listing the currently configured network connections (essentially the same output as that generated by the nmcli con show command):
Figure 23-1
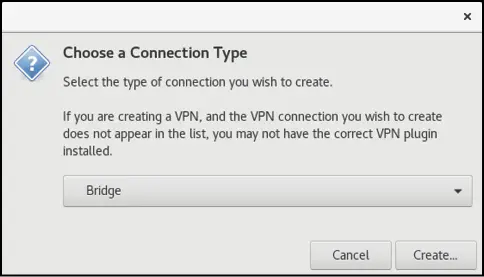
To create a new connection, click on the ‘+’ button located in the bottom left-hand corner of the window. From the resulting dialog (Figure 23-2) select the Bridge option from the menu:
Figure 23-2
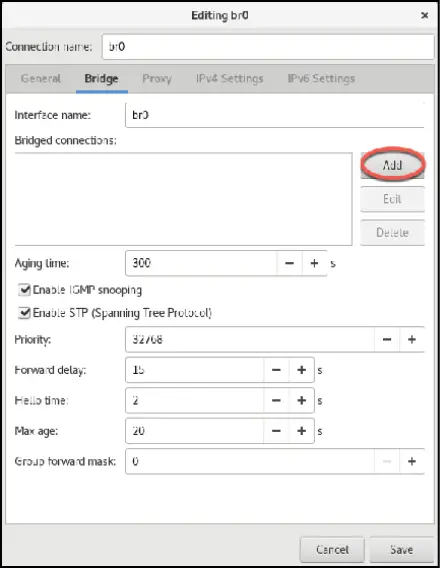
With the bridge option selected, click on the Create... button to proceed to the bridge configuration screen. Begin by changing both the connection and interface name fields to br0 before clicking on the Add button located to the right of the Bridge connections list as highlighted in Figure 23-3:
Figure 23-3
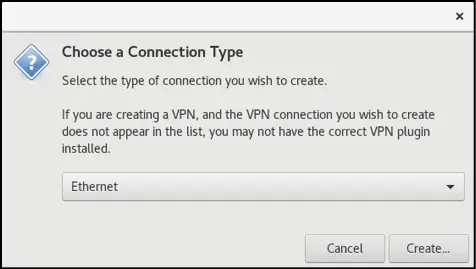
From the connection type dialog (Figure 23-4) change the menu setting to Ethernet before clicking on the Create... button:
Figure 23-4
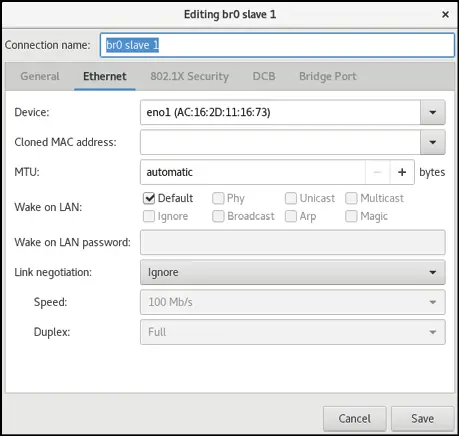
Another dialog will now appear in which the bridge slave connection needs to be configured. Within this dialog, select the physical network to which the bridge is to connect (for example eno1) from the Device menu:
Figure 23-5
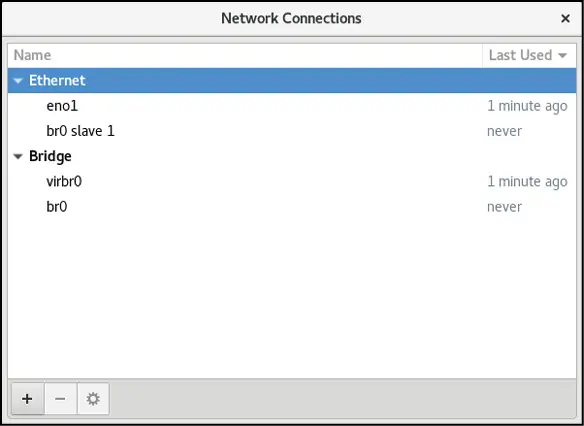
Click on the Save button to apply the changes and return to the Editing br0 dialog (as illustrated in Figure 23-3 above). Within this dialog, click on the Save button to create the bridge. On returning to the main window, the new bridge and slave connections should now be listed:
Figure 23-6
All that remains is to bring down the original eno1 connection and bring up the br0 connection using the steps outlined in the previous chapter (remembering to perform these steps in a shell script if the host is being accessed remotely):
# nmcli con down eno1 # nmcli con up br0
It will also be necessary, as it was when creating the bridge using the command-line tool, to add this bridge to the KVM network configuration. To do so, simply repeat the steps outlined in the section above entitled “Declaring the KVM Bridged Network”. Once this step has been taken, the bridge is ready to be used by guest virtual machines.
Summary
By default, KVM virtual machines are connected to a virtual network that uses NAT to provide access to the network to which the host system is connected. If the guests are required to appear on the network with their own IP addresses, the guests need to be configured to share the physical network interface of the host system. As outlined in this chapter, this can be achieved using either the nmcli or nm-connection-editor tools to create a networked bridge interface.
|
You are reading a sample chapter from the Red Hat Enterprise Linux 8 (RHEL 8) Essentials book. Purchase a full copy of Red Hat Enterprise Linux 8 (RHEL 8) Essentials in eBook ($9.99) or Print ($36.99) format Red Hat Enterprise Linux 8 Essentials Print and eBook (ePub/PDF/Kindle) editions contain 31 chapters and over 250 pages |
| Previous | Table of Contents | Next |
| Creating KVM Virtual Machines on RHEL 8 with virt-install and virsh | Managing KVM on RHEL 8 using the virsh Command-Line Tool |