Understanding Windows Server 2008 File and Folder Ownership and Permissions
| Previous | Table of Contents | Next |
| Using NET SHARE to Configure Windows Server 2008 File Sharing | Auditing Windows Server 2008 File and Folder Access |
<google>BUY_WINSERV_2008R2</google>
One of the key advantages offered by NTFS over the older FAT file system type is the concept of file and folder permissions and ownership. Through careful implementation and management, file and folder permissions on NTFS based file systems significantly increases the security of data stored on a Windows Server system. In addition, file and folder permissions augment the shared permissions discussed in previous chapters to provide finer grained control over access to shared files and folders.
This chapter of Windows Server 2008 Essentials will provide a detailed overview of file and folder permissions and ownership in the context of Windows Server 2008, including topics such as transfer of ownership and permission inheritance.
Ownership of Files and Folders
The owner of a file or folder is the user who has complete and full control over that file or folder in terms of being able to grant access to the resource, and also allow other users to take over the ownership of a file or folder. This is often, but not always, the creator of the file or folder and is governed by the location of where the file or folder is first created. Typically, the creator of the file or folder is, by default, initially designated as the owner. Ownership of a file or folder may be taken by an administrator, any user with Take ownership permission on the object in question or any user with the right to Restore Files and Directories which by default includes members of the Backup Operators group.
Taking and Transferring Windows Server 2008 File and Folder Ownership
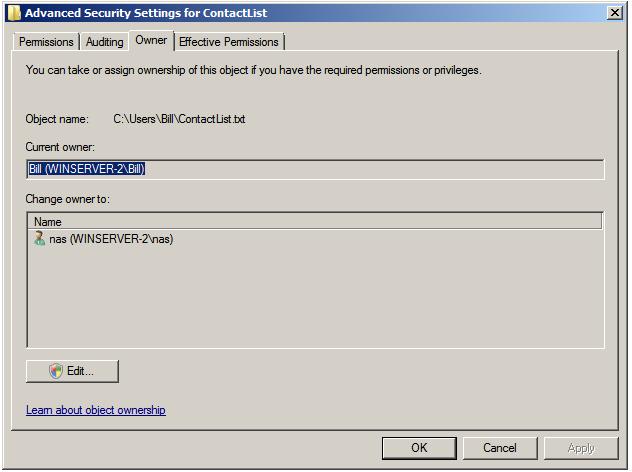
Ownership may be taken, when permitted, using the properties dialog of the file or folder in question. This can be accessed by right clicking on the file or folder in Windows Explorer, selecting Properties from the menu and then clicking on the Security tab. On the Security page of the properties dialog, click on the Advanced button to access the Advanced Security Settings dialog and then select the Ownership tab to display the following dialog:
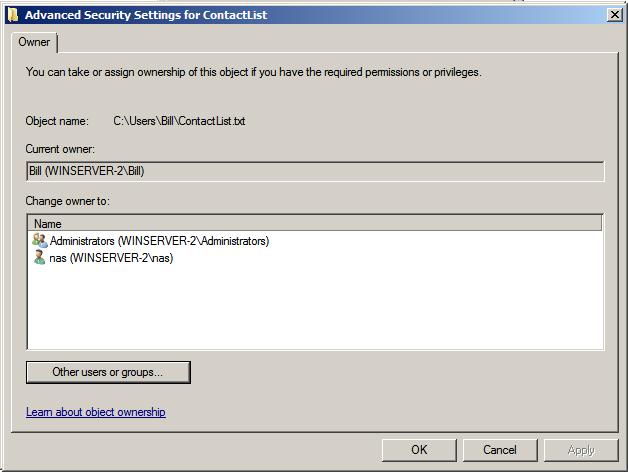
As illustrated in the preceding figure, the file's current owner is bill and the option is available for user nas to take over ownership of the file. To take ownership, click on the Edit button to display the following dialog box where ownership may be changed:
To take ownership, select your user name from the list and click on Apply. To transfer ownership to a different user, either select the name from the list, or search for the user by clicking on the Other users or groups... button. Select the required user and click on Apply to commit the transfer.
File and Folder Permission Inheritance
Another part of understanding file and folder permissions involves the concept of inheritance. When a file or sub-folder is created in an existing folder (referred to as the parent folder) it inherits, by default, all of the permissions of the parent folder. Similarly, when the permissions on a parent folder are changed, those changes are automatically inherited by all child files and folders contained within that parent folder.
To turn off inheritance for a child file or folder, right click the object in Windows Explorer, select Properties and then click on the Security tab of the properties dialog. On the Security properties panel, click on the Advanced button to display the Advanced Security Settings dialog followed by Edit... to display the editable permission settings. In this dialog, unset the check box next to Include inheritable permissions from parent object. Once selected, a warning dialog will appear providing the choice to retain the current inherited permissions, or to remove any inherited permissions keeping only permissions which have been explicitly set on the selected object:
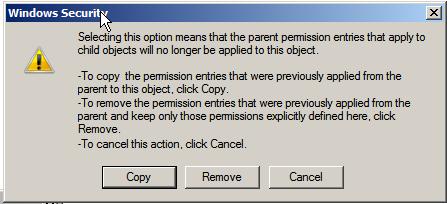
Occasionally, the converse situation exists, whereby a parent folder contains files and folders which have explicitly set permissions, rather than just the inherited permissions from the parent folder. In order to reset a folder and its children such that it only has inherited permissions, display the Security tab of the Properties dialog as outlined above, click on Advanced... and then Edit... and set the check box next to Replace all existing inheritable permissions on all descendants with inheritable permissions from this object. A dialog will subsequently appear warning that any explicitly defined permissions on all descendant files and folders will be removed and replaced by inheritable permissions. Click Yes to commit the change.
Basic File and Folder Permissions
NTFS provides two levels of file and folder permissions which can be used to control user and group access. These are basic permissions and special permissions. In essence, basic permissions are nothing more than pre-configured sets of special permissions. This section will look at basic permissions and the next will focus on special permissions and how they are used to create basic permissions.
The current basic permissions for a file or folder may be viewed by right clicking on the object in Windows Explorer, selecting Properties and then choosing the Security tab. At the top of the security properties panel is a list of users and groups for which permissions have been configured on the selected file or folder. Selecting a group or user from the list causes the basic permissions for that user to be displayed in the lower half of the dialog. Any permissions which are grayed out in the permission list are inherited from the parent folder.
The basic permission settings available differ slightly between files and folders. The following table lists the basic folder permissions supported by Windows Server 2008 on NTFS volumes:
| Permission | Description |
|---|---|
| Full Control | Permission to read, write, change and delete files and sub-folders. |
| Modify | Permission to read and write to files in the folder, and to delete current folder. |
| List Folder Contents | Permission to obtain listing of files and folders and to execute files. |
| Read and Execute | Permission to list files and folders and to execute files. |
| Write | Permission to create new files and folders within selected folder. |
| Read | Permission to list files and folders. |
The following table outlines the basic file permissions:
| Permission | Description |
|---|---|
| Full Control | Permission to read, write, change and delete the file. |
| Modify | Permission to read and write to and delete the file. |
| Read and Execute | Permission to view file contents and execute file. |
| Write | Permission to write to the file. |
| Read | Permission to view the files contents. |
To change the basic permission on a file or folder access the security panel of the properties dialog as outlined above and click Edit to display an editable version of the current settings. To change permissions for users or groups already configured, simply select the desired user or group from the list and change the settings in the permissions list as required (keeping in mind that any grayed out permissions are inherited from the parent folder). Click Apply to commit the changes.
To configure permissions for users or groups not already listed, click on the Edit... button on the security properties panel and click on Add.... Enter the names of users or groups separated by semi-colons (;) in the Select Users or Groups dialog box and then click on Check names to verify the names exist. Click on OK to confirm the user or group and return to the editing dialog. With the new user or group selected, configure the desired permissions and then Apply the settings when completed.
Special File and Folder Permissions
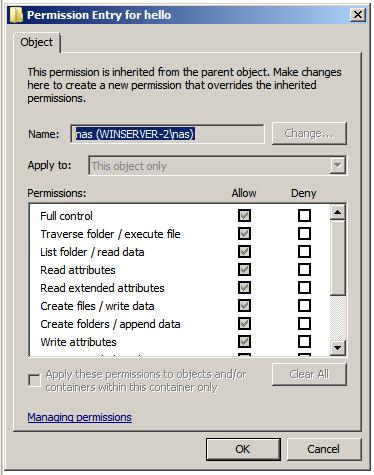
<google>WIN28BOX</google> As mentioned previously, basic file and folder permissions are really just pre-packaged collections of special permissions. Special permissions provide a much more fine grained approach to defining permissions on files and folders than is offered by basic permissions. The current special permissions configured on a file or folder can be viewed and modified by right clicking on the object in Windows Explorer, selecting Properties, clicking on the Security tab of the properties dialog and pressing the Advanced button. This will display the Permissions page of the Advanced Security Settings dialog which contains a list of users and groups for which permissions have been defined. Click on Edit to access the editable view of the permissions. Select a user or group from the list and click on the Edit... once again to display the Permission Entry for the selected user or group for this file or folder. This dialog will appear as illustrated in the following figure:
To change the special permissions simply make the appropriate selections in the list (keeping in mind that any grayed out permissions are inherited). To add special permissions for a user or group not currently listed in the Advanced Security Settings page, click on the Add... button and use the Select Users and Groups dialog to add new users or groups to the permission entries list.
Windows Server 2008 (or to be more exact, NTFS) provides 14 special permission options, each of which may be allowed or denied. The following table lists each of these settings and describes the option in more detail:
| Permission | Description |
|---|---|
| Traverse folder / execute file | Allows access to folder regardless of whether access is provided to data in folder. Allows execution of a file. |
| List folder / read data | Traverse folder option provides permission to view file and folder names. Read data allows contents of files to be viewed. |
| Read attributes | Allows read-only access to the basic attributes of a file or folder. |
| Read extended attributes | Allows read-only access to extended attributes of a file. |
| Create files / write data | Create files option allows the creation or placement (via move or copy) of files in a folder. Write data allows data in a file to be overwritten (does not permit appending of data). |
| Create folders / append data | Create folders option allows creation of sub-folders in current folder. Append data allows data to be appended to an existing file (file may not be overwritten) |
| Write attributes | Allows the basic attributes of a file or folder to be changed. |
| Write extended attributes | Allows extended attributes of of a file to be changed. |
| Delete subfolders and files | Provides permission to delete any files or sub-folders contained in a folder. |
| Delete | Allows a file or folder to be deleted. When deleting a folder, the user or group must have permission to delete any sub-folders or files contained therein. |
| Read permissions | Provides read access to both basic and special permissions of files and folders. |
| Change permissions | Allows basic and special permissions of a file or folder to be changed. |
| Take ownership | Allows user to take ownership of a file or folder. |
Effective File and Folder Permissions
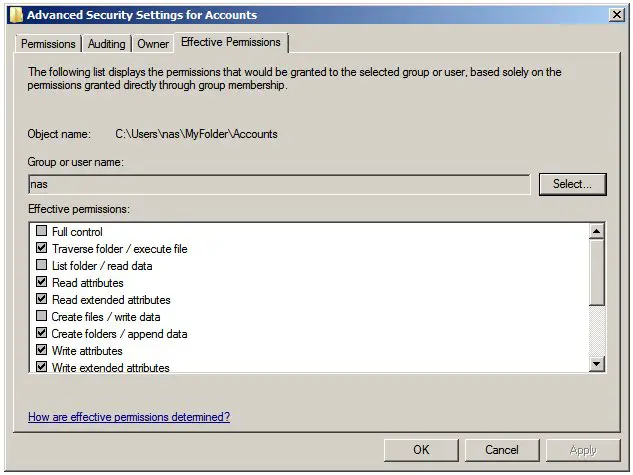
With all the different permission options provided by NTFS on Windows Server 2008, it can be difficult to determine how permissions may accumulate to affect a particular user or group for any given file or folder. In order to make this task a little easier, Windows provides a feature known as Effective Permissions which will list the cumulative permissions for a user or group. To access this feature, right click on the required file or folder in Windows Explorer, select Properties and then select the Security tab in the resulting properties dialog. Within the security panel, click on Advanced and select the Effective Permissions tab in the Advanced Security Settings dialog. The next step is to specify the user or group for which the effective permissions are to be calculated. To achieve this, click on the Select button and use the Select User or Group dialog to specify or search for a particular user or group and then click on OK. The effective permissions for the chosen user or group will subsequently be displayed, as illustrated below:
<google>BUY_WINSERV_2008R2_BOTTOM</google>